Table of Contents

Digital transformation and cloud migration are common terms that you’ll hear when referring to secure data and actions in modern business settings. In the past, businesses relied on on-premise systems to manage their network of computers and software, but these days, being fully integrated in the cloud is a necessity regardless of the industry. Cloud computing gives organizations access to high-performance computing power, unlimited storage, and robust data security for a fraction of the cost of on-premise systems.
Cloud computing data security plays a critical role in safeguarding sensitive information and ensuring the privacy and integrity of data stored in the cloud. As more businesses adopt cloud-based solutions, understanding the principles and benefits of cloud data security becomes increasingly important. Businesses also have to ensure that they recognize and prepare to meet challenges that are likely to arise with regard to balancing productivity levels and security when moving to the cloud. Moving from on-premise systems to cloud-based systems requires a proper approach to ensure that organizational security remains intact during and after the transition.
This article explores what cloud computing data security entails and why companies need robust security measures in place. We will also discuss the principles of data security in cloud computing, covering aspects such as data confidentiality, integrity, and availability.
What is Data Security in Cloud Computing?
Cloud computing data security refers to the protection of data stored, processed, and transmitted within cloud environments. It involves implementing a range of security measures and technologies to mitigate risks and ensure the confidentiality, integrity, and availability of data. Cloud data security encompasses various aspects, including access control, encryption, data backup, and incident response.
Access Control and Encryption
One critical aspect of data security in cloud computing is access control. Access control mechanisms are put in place to manage and restrict user access to sensitive data stored in the cloud. This includes authentication processes, authorization levels, and user permissions. Organizations can prevent unauthorized access and data breaches by implementing robust access control measures.
Another important component of data security in cloud computing is encryption. Encryption involves converting data into a coded format that can only be accessed with the appropriate decryption key. This helps protect data at rest and in transit within the cloud environment. Strong encryption algorithms are used to safeguard sensitive information from unauthorized disclosure or tampering.
Why Companies Need Cloud Computing Data Security
In today’s digital landscape, where data breaches and cyber threats are prevalent, companies cannot afford to overlook the importance of cloud computing data security. Many businesses are leveraging cloud computing for its scalability, flexibility, and cost-effectiveness. However, without robust security measures, sensitive information is susceptible to unauthorized access, theft, or corruption.
By implementing stringent data security measures, companies can mitigate the risks associated with cloud computing for data security and protect valuable assets. Effective cloud computing and data security measures within cloud instances safeguard confidential information, enhance customer trust, comply with regulatory requirements, and minimize financial and reputational damage caused by data breaches.
Encryption is an essential part of this process. Proper encryption of data ensures that even if data is intercepted, it remains unreadable to unauthorized users. Additionally, companies can implement multi-factor authentication protocols to add an extra layer of security, requiring users to provide multiple forms of verification before accessing sensitive information.
In addition, administrators can limit user access to certain aspects of a system based on the Zero Trust principles, which is described in more detail in the table below:
| Zero Trust Principle | Meaning |
| Verify explicitly | Authentication is taken very seriously, and every user is authenticated based on all available data points, including user identity, location, device, service or workload, data classification, and anomalies. |
| Use least privilege access | Each user only receives the access privileges that they need to do their work, which is referred to as “just enough access.” Risk-based adaptive policies like this, as well as data protection measures, help secure data and productivity. |
| Always assume a breach | When you always assume a breach, you minimize the blast radius and segment access. End-to-end encryption verification and analytics give you visibility, drive threat detection, and help you improve your defenses. |
Regular security audits and penetration testing are other essential components of a comprehensive cloud computing data security strategy. These measures help identify vulnerabilities in the system and address them proactively, reducing the likelihood of successful cyber attacks. By staying proactive and continuously updating security protocols, companies can stay one step ahead of cyber threats and protect their data assets effectively.
Principles of Data Security In Cloud Computing
When it comes to data security in cloud computing, several principles guide the implementation of effective security measures:
- Data confidentiality: Cloud providers should ensure that data remains confidential and can only be accessed by authorized individuals or entities. This principle involves implementing access controls, encryption, and secure data transmission protocols.
- Data integrity: To ensure data integrity, cloud providers must prevent unauthorized modification, corruption, or deletion of data. Techniques such as checksums, digital signatures, and encryption can help detect and protect against data tampering.
- Data availability: Cloud services should be highly available, ensuring authorized users can access data whenever needed. Redundancy, failover mechanisms, and disaster recovery strategies play a vital role in maintaining data availability.
Another crucial aspect of data security in cloud computing is network security. This involves protecting the cloud infrastructure from unauthorized access, cyber-attacks, and other security threats. Network security measures include firewalls, intrusion detection systems, and virtual private networks (VPNs) to create secure communication channels.
Additionally, Compliance and Regulatory Requirements are essential considerations in data security within cloud computing. Cloud providers must adhere to industry-specific regulations and standards to ensure the protection of sensitive data. Compliance frameworks such as GDPR, HIPAA, and PCI DSS outline data handling, storage, and transmission requirements in the cloud environment.
Benefits of Cloud Data Security

Implementing robust cloud data security measures offers numerous benefits for businesses:
- Greater visibility: Cloud data security solutions provide organizations with enhanced visibility into their data, allowing them to track and monitor user activities, detect anomalous behavior, and respond swiftly to potential security incidents.
- Easy backups and recovery: Cloud data security solutions often include automated backup and recovery capabilities, eliminating the need for manual backups and reducing the risk of data loss in the event of system failures or errors.
- Cloud data compliance: With data privacy regulations becoming increasingly strict, cloud data security solutions assist businesses in achieving compliance with industry-specific regulations and standards. These solutions often offer built-in controls and frameworks to ensure legal and regulatory requirements adherence.
Cloud computing data security measures can also enhance collaboration and productivity within organizations. By securely storing data in the cloud, employees can access information from anywhere, at any time, using any device with an internet connection. This flexibility promotes remote work capabilities and facilitates seamless collaboration among team members located in different geographical locations.
Another advantage of robust cloud data security is the scalability it offers to businesses. As companies grow and their data storage needs increase, cloud solutions can easily scale up to accommodate additional data without the need for significant infrastructure investments. This scalability ensures that businesses can adapt to changing data requirements quickly and efficiently without experiencing downtime or performance issues.
1. Data Encryption
Data encryption is a fundamental aspect of cloud data security. By encrypting data at rest and in transit, organizations ensure that even if unauthorized individuals gain access to the data, they cannot read or modify it without the encryption keys. Encryption algorithms and protocols, such as AES and SSL/TLS, are commonly employed to protect sensitive information.
One of the key advantages of using data encryption in cloud security is its ability to provide an additional layer of protection for sensitive information. In addition to securing data from external threats, encryption also helps organizations comply with various data protection regulations and standards, such as GDPR and HIPAA. This ensures that companies handling personal or confidential data meet the necessary requirements to safeguard the privacy and integrity of the information.
The process of encrypting data involves converting the information into a code that can only be deciphered with the corresponding decryption key. This means that even if a data breach occurs, the stolen data remains incomprehensible and unusable to unauthorized parties. By implementing robust encryption practices, organizations can significantly reduce the risk of data breaches and mitigate the potential impact of security incidents on their operations and reputation.
2. Lower Costs
In addition to providing improved security, cloud data security solutions can also lead to cost savings for businesses. By leveraging cloud services and security features, organizations can reduce the need for expensive on-premises infrastructure, hardware maintenance costs, and staffing requirements for managing security measures.
Furthermore, the scalability of cloud data security solutions allows businesses to adjust their resources based on demand, leading to more efficient use of resources and cost optimization. This flexibility enables companies to easily scale up or down based on their needs, avoiding the need to over-provision resources that may go underutilized, ultimately saving on unnecessary expenses.
Most cloud data security providers often offer subscription-based pricing models, allowing businesses to pay only for the required services and features. This pay-as-you-go approach eliminates the need for large upfront investments in security infrastructure, making it a more cost-effective option for organizations of all sizes.
Additionally, with cloud data security, businesses can benefit from automatic software updates and maintenance, reducing the burden on internal IT teams and further cutting down on operational costs.
3. Advanced Incident Detection and Response
The ability to detect security incidents promptly and respond effectively is crucial in minimizing the impact of potential breaches. Cloud data security solutions often feature advanced threat detection and incident response capabilities, enabling organizations to identify and resolve security issues swiftly, thereby reducing the potential damage caused by breaches.
One key aspect of advanced incident detection in cloud data security is the utilization of machine learning algorithms. These algorithms can analyze vast amounts of data in real-time to identify patterns and anomalies that may indicate a security threat. By continuously learning from new data and adapting to evolving threats, machine learning algorithms enhance the overall effectiveness of incident detection in cloud environments.
In addition to machine learning, cloud data security solutions also leverage threat intelligence feeds from various sources. These feeds provide up-to-date information on emerging threats and vulnerabilities, allowing organizations to proactively defend against potential attacks. Organizations can stay ahead of cyber threats by integrating threat intelligence into their security systems and strengthening their incident response capabilities.
Importance of Compliance and Certification in Cloud Data Security

Compliance and certification play a pivotal role in ensuring the effectiveness and trustworthiness of cloud data security solutions. By adhering to recognized standards and obtaining certifications, cloud providers demonstrate their commitment to meeting rigorous security requirements and safeguarding customer data.
Ensuring compliance and obtaining certifications in cloud data security is not just a matter of meeting regulatory requirements; it is also about building trust with customers. When a cloud provider invests time and resources into achieving certifications like ISO27001, SOC2, or HIPAA, they clearly tell their clients that they take data security seriously and are willing to undergo external validation to prove their commitment.
Several key compliance and certification standards are relevant to cloud data security, as described in the table below:
| Certification standard | Description |
| ISO27001 | This is an international standard that outlines requirements for establishing, implementing, maintaining, and continuously improving an information security management system. Compliance with this standard demonstrates a cloud provider’s commitment to managing risks and protecting customer data. |
| SOC2 (Service Organization Control 2) | This is an auditing standard developed by the American Institute of CPAs (AICPA). It assesses a cloud provider’s controls related to security, availability, processing integrity, confidentiality, and privacy. |
| HIPAA | The Health Insurance Portability and Accountability Act (HIPAA) establishes standards for protecting sensitive health information. Organizations handling healthcare data must comply with HIPAA requirements to ensure the security and privacy of protected health information. |
| ITAR | The International Traffic in Arms Regulations (ITAR) controls the export and import of defense-related articles and services. Cloud providers hosting ITAR-regulated data need to implement strict security measures, access controls, and auditing capabilities to comply with ITAR requirements. |
When it comes to ITAR compliance in cloud data security specifically, encryption plays a crucial role. Encryption helps protect sensitive ITAR-regulated data from unauthorized access or breaches. Cloud providers often use advanced encryption algorithms to secure data both at rest and in transit, ensuring that the information remains confidential and secure. In addition to encryption, data residency is another key aspect of ITAR compliance in cloud data security:
- ITAR regulations require that ITAR-regulated data be stored and processed within the United States or approved territories.
- Cloud providers must have mechanisms in place to ensure that ITAR data does not leave the authorized geographic boundaries, thereby maintaining compliance with ITAR regulations.
Obtaining these certifications involves rigorous assessments, audits, and ongoing compliance efforts. Cloud providers must continuously monitor and improve their security practices to maintain these certifications, demonstrating a commitment to staying ahead of evolving threats and industry best practices. By adhering to these standards, cloud providers not only enhance their own security posture but also contribute to raising the overall level of trust and security in the cloud computing ecosystem.
Challenges of Data Security in the World of Cloud Computing & How NZO Cloud Helps
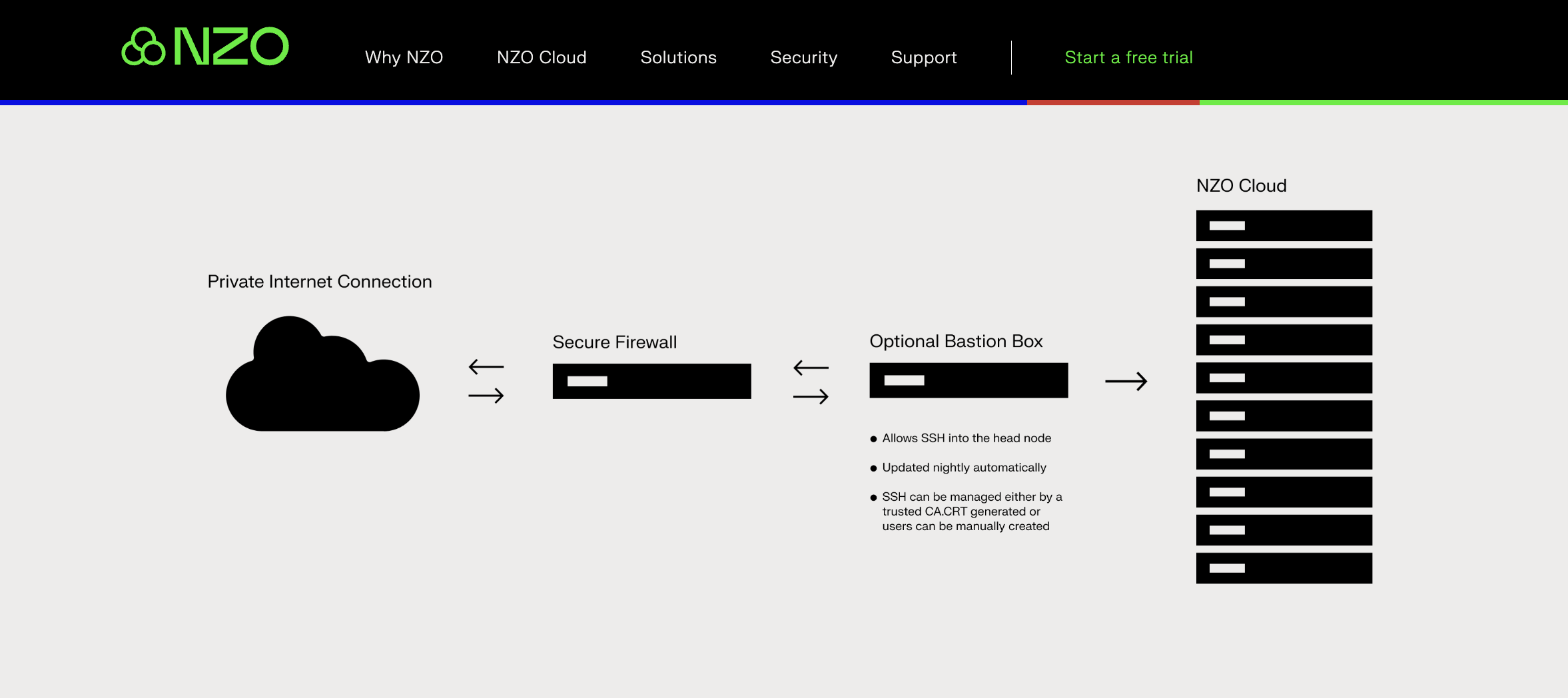
Data security in the realm of data security and cloud computing presents a myriad of challenges that organizations must navigate to safeguard sensitive information effectively. As businesses increasingly rely on cloud-based services to store, process, and transmit data, they encounter several key challenges:
- Data breaches: Cloud environments are prime targets for cyber attacks and data breaches. Threat actors exploit vulnerabilities in cloud infrastructure or employ sophisticated techniques like phishing and malware to gain unauthorized access to sensitive data.
- Identity and Access Management (IAM): Managing user identities and access privileges across diverse cloud services and applications is complex. Weak authentication mechanisms or improper access controls can lead to unauthorized data access and breaches.
- Data loss: Data loss incidents, whether due to accidental deletion, hardware failure, or malicious activity, are a constant threat in cloud environments. Organizations must implement robust backup and recovery mechanisms to mitigate the risk of data loss.
- Insider threats: Malicious or negligent insiders pose a significant security risk in cloud environments. Employees or contractors with privileged access may intentionally or inadvertently compromise sensitive data, emphasizing the need for stringent monitoring and access controls.
- Shared responsibility model: Cloud service providers typically operate under a shared responsibility model, where they secure the underlying infrastructure while customers are responsible for securing their data and applications. This shared responsibility can lead to confusion or gaps in security coverage if roles and responsibilities are not clearly defined.
- Data encryption: Protecting data both at rest and in transit is essential to prevent unauthorized access. However, implementing strong encryption measures without impacting performance or usability can be challenging.
- Security misconfigurations: Improperly configured cloud services or mismanaged security settings are a common cause of data breaches. Organizations must continuously monitor and audit their cloud environments to detect and remediate security misconfigurations promptly.
With NZO Cloud, businesses can benefit from:
- Tailored deployment: Say goodbye to the one-size-fits-all approach. NZO Cloud crafts a bespoke deployment that aligns perfectly with your business requirements. No need to shoehorn your processes into predefined templates – get exactly what you need, tailored to your specifications.
- Transparent pricing: Hidden costs associated with storage and data transfer can quickly eat up your budget. Unlike the ambiguous pay-per-use models offered by major high-performance computing and cloud data security providers, NZO Cloud operates on standardized subscription pricing. This means you’ll always have clarity on your costs, allowing for better budget management without any hidden surprises.
- Dedicated support: When dealing with tech giants like Google, Microsoft, or Amazon, obtaining personalized support can be a challenge due to their sheer scale. NZO Cloud offers ongoing assistance with dedicated onboarding and security engineering teams at your disposal. Rest assured, your cloud infrastructure will receive the attention and support it deserves to ensure smooth operations.
Conclusion
Cloud computing data security is essential for businesses seeking to protect their valuable assets and maintain compliance with regulatory requirements. By understanding the principles and benefits of cloud data security, companies can make informed decisions regarding their data storage and processing strategies. Deploying robust security measures, including encryption, access controls, and incident response mechanisms, ensures data confidentiality, integrity, and availability in cloud environments. Additionally, achieving compliance with recognized standards and obtaining certifications helps build customer trust and assurance. By prioritizing cloud computing data security, businesses can confidently leverage the benefits of cloud computing while minimizing potential risks.
By implementing robust security measures such as access control, encryption, and incident response, businesses can mitigate the risks associated with cloud computing and protect their valuable assets. Compliance with industry standards and certifications further enhances the credibility and trustworthiness of cloud data security solutions.
However, navigating the complexities of data security and cloud computing presents challenges, including data breaches, identity and access management, and security misconfigurations. Despite these challenges, businesses can leverage solutions like NZO Cloud to address their security needs effectively.
With tailored deployment, transparent pricing, and dedicated support, NZO Cloud offers businesses a reliable and scalable solution for managing their cloud infrastructure securely. By partnering with NZO Cloud, organizations can confidently navigate the intricacies of cloud data security and ensure the integrity and confidentiality of their data assets.
Reach out to us today for a free trial to discover how we can help you build your cloud security solution for your business.